Encryption is one of the core foundations of modern digital security. It ensures that sensitive data remains protected, even if intercepted by unauthorized parties. Let’s break down what encryption is, how it works, and why it’s so essential. 🔻
📌 What is Encryption?
Encryption is the process of converting information or data into a code to prevent unauthorized access. It uses mathematical algorithms to transform plain, readable data (plaintext) into an unreadable format (ciphertext). Only those with the correct key can decode and access the original information.
📌 How Does Encryption Work?
Encryption uses algorithms and keys to secure data. The sender encrypts the data using a specific algorithm and a key. The receiver, who also has access to the key, can then decrypt the data and view the original content.
There are two main types of encryption: symmetric and asymmetric.
📌 Types of Encryption
-
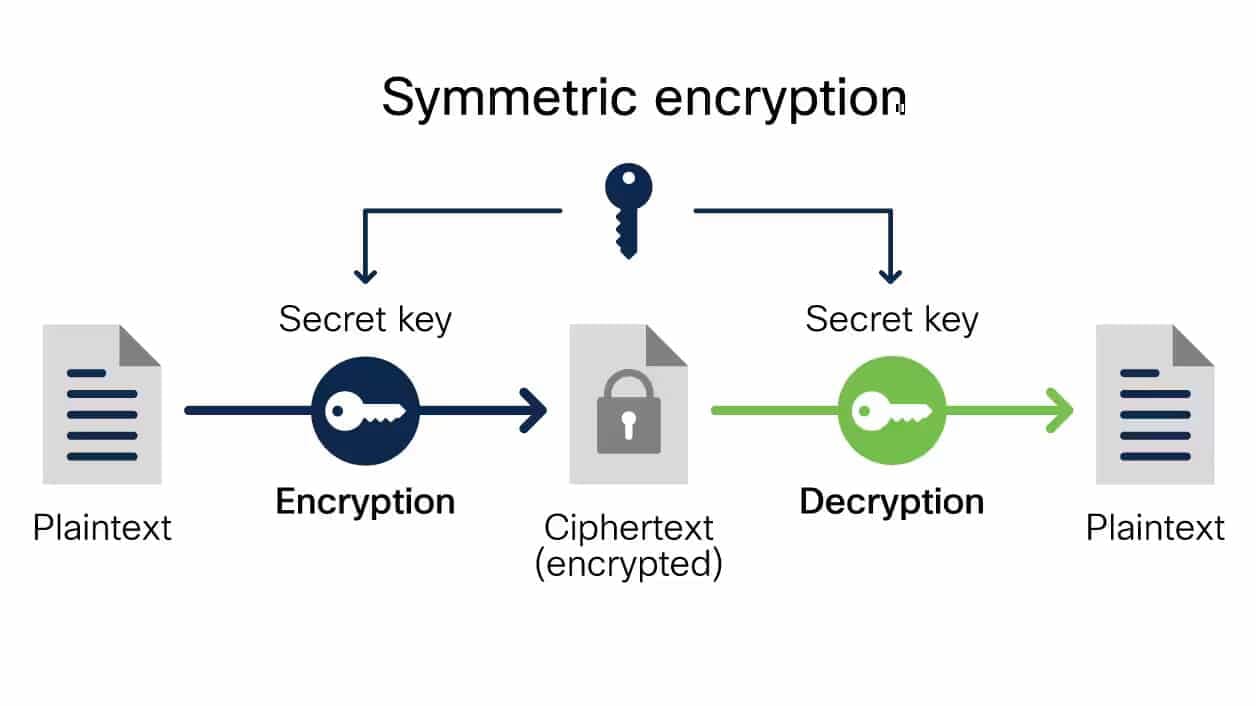
Symmetric Encryption:
In symmetric encryption, the same key is used to both encrypt and decrypt data. This method is fast and efficient but requires a secure method of sharing the key between parties. Examples of symmetric encryption algorithms include AES (Advanced Encryption Standard) and DES (Data Encryption Standard).
Example in JavaScript:
1const crypto = require('crypto'); 2const algorithm = 'aes-256-cbc'; 3const key = crypto.randomBytes(32); // Generate a 32-byte key 4const iv = crypto.randomBytes(16); // Initialization vector 5 6// Encrypt function 7function encrypt(text) { 8 const cipher = crypto.createCipheriv(algorithm, key, iv); 9 let encrypted = cipher.update(text, 'utf-8', 'hex'); 10 encrypted += cipher.final('hex'); 11 return { iv: iv.toString('hex'), encryptedData: encrypted }; 12} 13 14// Decrypt function 15function decrypt(encryptedData, iv) { 16 const decipher = crypto.createDecipheriv(algorithm, key, Buffer.from(iv, 'hex')); 17 let decrypted = decipher.update(encryptedData, 'hex', 'utf-8'); 18 decrypted += decipher.final('utf-8'); 19 return decrypted; 20} 21 22// Example usage 23const message = "Hello, Encryption!"; 24const encrypted = encrypt(message); 25console.log("Encrypted:", encrypted); 26 27const decrypted = decrypt(encrypted.encryptedData, encrypted.iv); 28console.log("Decrypted:", decrypted); 29 -
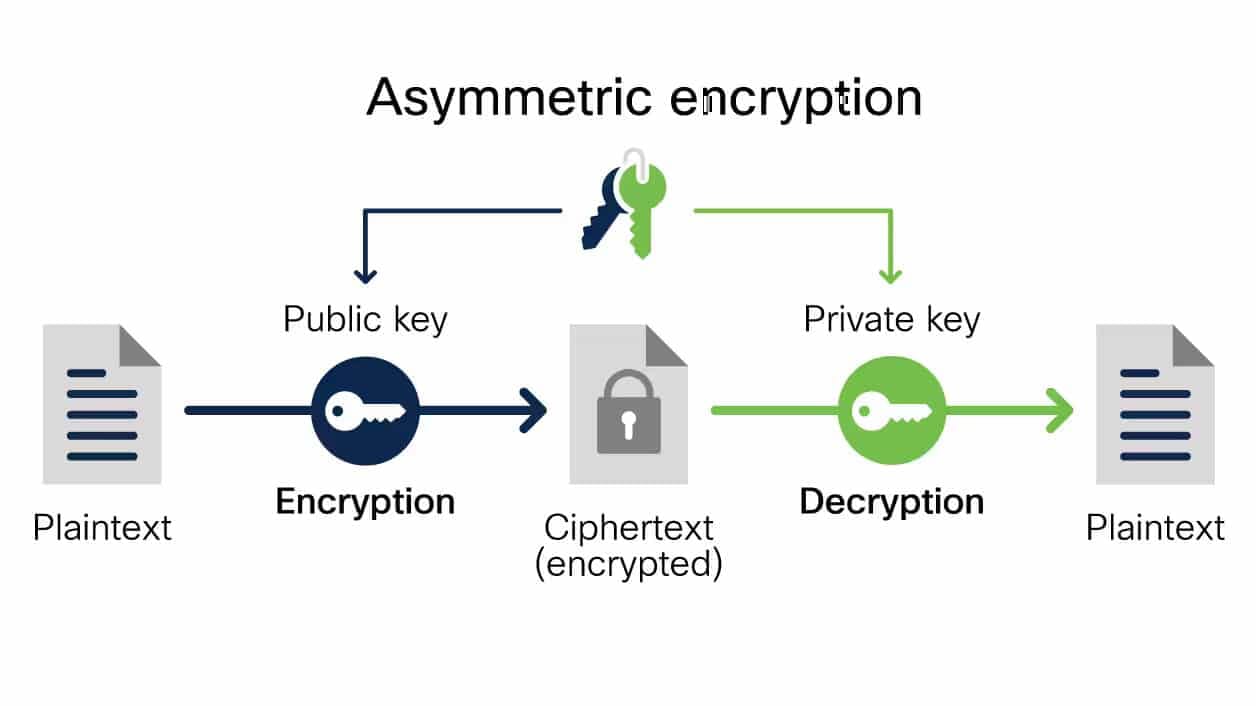
Asymmetric Encryption:
Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. This method is more secure for exchanging information, as the public key can be shared openly while the private key remains secret. Popular algorithms include RSA and Elliptic Curve Cryptography (ECC).
Example in JavaScript:
1const { generateKeyPairSync, publicEncrypt, privateDecrypt } = require('crypto'); 2 3// Generate a pair of RSA keys 4const { publicKey, privateKey } = generateKeyPairSync('rsa', { 5 modulusLength: 2048, 6 publicKeyEncoding: { type: 'spki', format: 'pem' }, 7 privateKeyEncoding: { type: 'pkcs8', format: 'pem' }, 8}); 9 10// Encrypt function using the public key 11function encrypt(text) { 12 return publicEncrypt(publicKey, Buffer.from(text)); 13} 14 15// Decrypt function using the private key 16function decrypt(encryptedText) { 17 return privateDecrypt(privateKey, encryptedText).toString(); 18} 19 20// Example usage 21const message = "Secure Message!"; 22const encrypted = encrypt(message); 23console.log("Encrypted:", encrypted.toString('hex')); 24 25const decrypted = decrypt(encrypted); 26console.log("Decrypted:", decrypted); 27
📌 Properties That Differentiate Encryption from Encoding and Hashing
- Purpose:
- Encryption: The main goal is to protect data confidentiality. Data is scrambled into an unreadable format and can only be decrypted with the correct key.
- Encoding: It focuses on data representation for compatibility and storage purposes, not security.
- Hashing: Used for data integrity. It creates a fixed-size output from input data, and this process is typically irreversible.
- Reversibility:
- Encryption: It is reversible, but only with the correct decryption key.
- Encoding: Always reversible using the proper decoding method.
- Hashing: It is a one-way operation; once data is hashed, it cannot be restored to its original form.
- Use Cases:
- Encryption: Used for secure communication, protecting sensitive data, and online transactions.
- Encoding: Used for data compression, safe transmission of URLs, or file storage.
- Hashing: Used for password storage, data integrity checks, and creating unique identifiers.
📌 Why is Encryption Important?
✅ Data Confidentiality: Encryption ensures that only authorized parties can access sensitive data, protecting it from unauthorized access.
✅ Secure Communication: From emails to online banking, encryption safeguards communication over public networks.
✅ Data Integrity: Some encryption algorithms also provide data integrity checks, ensuring that data hasn’t been tampered with during transmission.
✅ User Trust: Encryption builds trust with users by ensuring their personal and financial information is secure.
📌 How to Create an Encryption Algorithm
Designing your own encryption algorithm is an extremely complex task that requires a deep understanding of cryptographic principles, mathematics, and security considerations. However, here’s a simplified breakdown of what is needed to understand how encryption algorithms are created.
📌 Key Concepts Needed to Create an Encryption Algorithm
- Mathematical Foundations:
- Number Theory: Encryption algorithms rely on complex mathematical structures such as prime numbers, modular arithmetic, and finite fields.
- Algebraic Structures: Concepts like rings, groups, and fields are essential for designing secure cryptographic algorithms.
- Probability and Statistics: Understanding randomness and probability distributions is crucial for ensuring that encrypted data cannot be easily predicted.
- Core Components:
- Plaintext and Ciphertext: The original data (plaintext) needs to be transformed into a secure, unreadable format (ciphertext) using a specific algorithm.
- Keys: Keys are essential to the encryption process. The strength of an encryption algorithm often depends on the size and randomness of the key.
- Algorithms: At the heart of encryption are mathematical functions that mix and transform the data in secure ways. Examples include substitution-permutation networks and modular exponentiation.
- Types of Transformations:
- Substitution: Replacing elements of the plaintext with other elements based on a certain rule.
- Permutation: Rearranging the elements of the plaintext in a specific order to obscure the original message.
- Mixing: Combining the above transformations in complex patterns to increase the difficulty of deciphering the text without the key.
- Security Considerations:
- Avalanche Effect: A small change in the plaintext or the key should result in a large, unpredictable change in the ciphertext.
- Key Length: The key must be long enough to resist brute-force attacks.
- Randomness: The algorithm should include elements of true randomness to make guessing or predicting the key virtually impossible.
- Testing and Analysis:
- Cryptanalysis: Techniques used to test the strength of an encryption algorithm against attacks.
- Peer Review and Standards: Algorithms must be reviewed by the cryptographic community and follow established standards like those set by organizations such as NIST.
📌 Example: Building a Simple Custom Encryption Algorithm
Here’s a simplified example in JavaScript of creating a basic encryption algorithm:
1// A simple encryption function using XOR (not secure for real use) 2function simpleEncryptDecrypt(text, key) { 3 let result = ''; 4 for (let i = 0; i < text.length; i++) { 5 // XOR each character with the key character 6 result += String.fromCharCode(text.charCodeAt(i) ^ key.charCodeAt(i % key.length)); 7 } 8 return result; 9} 10 11// Usage Example 12const key = "mySecretKey"; 13const message = "Hello, world!"; 14const encrypted = simpleEncryptDecrypt(message, key); 15console.log("Encrypted Message:", encrypted); 16 17const decrypted = simpleEncryptDecrypt(encrypted, key); 18console.log("Decrypted Message:", decrypted); 19
Explanation:
- XOR Cipher: This example uses a simple XOR cipher, where each character of the message is XORed with a character from the key. While it demonstrates how encryption works, it is not secure for real-world applications.
- Reversibility: Applying the XOR operation twice with the same key returns the original text, making it reversible.
📌 Potential Challenges in Encryption
- Key Management: Losing or exposing the encryption key can make the data unrecoverable or vulnerable.
- Performance: Encryption can slow down performance, especially with large amounts of data or high-security algorithms.
- Complexity: Implementing encryption properly requires a good understanding of cryptographic principles, or it may introduce vulnerabilities.
Encryption is a fascinating and essential area of digital security. By understanding how it works and the principles behind it, we can better appreciate the security measures that protect our data every day.
